Video editing software doesn't have to be expensive. Whether you're an experienced home videographer or making your first foray into filmmaking, some of the best video editing software is yours to download and use completely free.
If you just want to cut a clip to size or add a new soundtrack, there are lightweight editors that will help you get the job done in seconds, and export the video in a format suitable for uploading online, or playing on any desktop or mobile device.
Alternatively, if you're looking for more advanced tools like chroma keying and color grading, there are also advanced programs that offer everything you'd expect to find in premium software – except the price tag.
However, not all videos editors are created equal. Some prevent you exporting projects longer than a couple of minutes, offer a very small selection of editing tools, or add unsightly watermarks to your finished work. Here we've rounded up only the software that delivers on its promises, making video editing easy and fun, with no compromises.
1. Lightworks
Puts professional quality tools within the reach of everyone – regardless of budget. The best free video editor available
Lightworks is far more than a simple application for combining video clips and applying filters; it's been used to produce Hollywood movies including The King's Speech and Road to Perdition.
Lightworks is described as the professional video editor for everyone, and we reckon that's a fair summary. Despite its power, it will run well on fairly modest hardware, and it handles video capture and advanced editing with aplomb.
If you've tried other free video editors you'll probably find that the interface is a little different to anything you're used to, but you can arrange the various controls and windows to create something that suits your way of working.
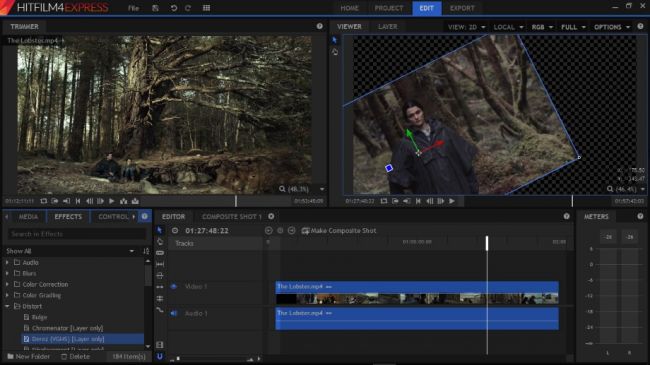
2. Hitfilm Express
A powerful free video editor that's expandable if you outgrow it
Hitfilm Express is another video editor that promises pro-level features for free – and it delivers. The basic editor is very impressive, with advanced cutting tools, a great set of audio and video filters, layers and masking, compositing options, and chroma keying for creating green screen effects.
Additional tools are available for a fee, starting at $10 for a pack featuring color-correction, exposure adjustment, split screen masking, and various creative filters.
The downside of all this power is that Hitfilm Express is much more demanding than either Lightworks or Shotcut. Make sure you check the technical requirements before downloading it to avoid disappointment.
3. DaVinci Resolve
Premium quality software for advanced video and audio editing
DaVinci Resolve is a professional-grade video editor, with intuitive interfaces for editing, color correction, audio mastering and exporting. There's the usual multi-track timeline for arranging video and audio clips, plus context-sensitive trimming, and a vast collection of filters and effects.
Color correction is one of DaVinci Resolve's standout features, whether you want to adjust a whole video or just a selected part. There's HDR support, and you can work on raw files directly from your camera.
A few of the filters are exclusive to the premium DaVinci Resolve Studio, and there's a maximum export resolution of 3,840 x 2,160, but those are the only limitations. It's overkill if you just want to trim a video and upload it to YouTube, but for bigger projects DaVinci Resolve is hard to beat.
4. Shotcut
It might look unusual, but master it and you'll reap the benefits
Shotcut is another professional-feeling free video editor that requires a little patience if you are achieve the results it is so capable of delivering. The slightly unusual interface can be put down to the fact that this started life as a Linux application, and little has changed in its conversion to Windows.
To start with, the interface may seem a little stark. You will need to not only load a video, but also choose which editing mode you would like to work in and which tools you'd like to use.
There's no getting away from the fact that Shotcut has a steep learning curve. It's possible to achieve some impressive results by simply applying one of its many filters to your video, but the real rewards will only be reaped by those willing to invest the time and energy in fully getting to grips with what's on offer.
5. VSDC Free Video Editor
A non-linear editor stacked with tools, with more added all the time
VSDC Free Video Editor provides a huge array of effects and filters to enhance your footage, with both wizards and manual options to suit beginners or more advanced users.
VSDC is highly capable, and can yield superb results. As a non-linear editor, it works in rather a different way to many other similar tools, letting you position clips and other elements on the timeline wherever you like and edit them there.
With the ability to not only work with multiple scenes and transitions, but also to add sprites and text to videos, you can create a professional-quality movie if you're willing to stick with VSDC's slightly odd way of working and unusual interface.
The latest version of VSDC adds extra artistic effects, including smoke. There's also a dedicated Instagram export profile and automatic image stabilization. It's noticeably faster, too. An excellent choice for creative video projects.