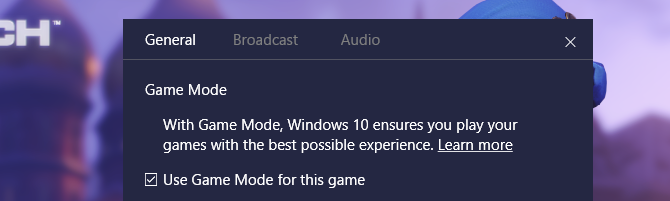
1. Turn On Game Mode
The latest version of Windows 10, the Creators Update, adds a new feature known as Game Mode. There’s no way to perpetually run in Game Mode, unfortunately, but you can activate it with a simple key combination of the Windows Key + G. However, you must first enable Game Mode.
To enable Game Mode (it’s only available in Windows 10 Creators Update) open Settings > Gaming and choose Game Mode. Turn on Use Game Mode. It’s only supposed to be used for games, but you can activate it whenever you need to get a little burst of speed. It’s particularly useful if you have a lot of background apps that are dragging down a resource-intensive program.
2. Turn Off Visual Effects
Windows offers a really easy way to shut off all visual enhancements. Simply navigate to System > Advanced system settings and choose Advanced from the tabs above. Under Performance, choose Settings. Then check the radio button for Adjust for best performance to shut off all visual effects.
I have visual effects disabled on a few systems and it seems to make a big impact, particularly on older computers. On the downside, things won’t look as nice. I advise leaving Smooth edges of screen fonts enabled as it helps when reading text.
3. Speed Up Your Processor
Windows possesses three predefined settings (at least) for how your processor scales its frequency up to run processes. The three defaults are Balanced, High performance, and Power saver. (Sometimes manufacturers also include custom plans here.) You are almost always better off on a laptop using Balanced or Power saver, but High performance — as the name suggests — makes Windows faster. Because it consumes the most amount of power it’s also more appropriate for desktops. Choose it if you want to get the most juice out of your computer.
4. Turn Off Startup Programs
About half of the programs that I install try to run silently in the background. That’s fine for just a handful of programs, but the effect on performance is cumulative. If your computer has enough programs set to run at startup, the entire system will bog down. Getting rid of non-essential startup software is absolutely essential for performance.
Press the key combination of Ctrl + Alt + Delete to enter Windows Task Manager. Choose Task Manager from the menu that pops up. Then select the Startup tab from the top of the screen. From the Startup tab, you can eliminate most auto-starting applications. The majority of apps out there don’t need to run in the background, unless they came preinstalled with your computer (and even these are oftentimes bloatware).
5. Malware Scanner
We’ve written to death the subject of malware scanners for good reason: most performance problems originate with malignant programs running wild in the background. Some of the better free malware scanners out there include Malwarebytes, SuperAntiSpyware, and ClamWin.
6. Registry Cleaner
The Windows registry keeps a manifest of settings for Windows and other programs. Oftentimes, programs make changes to the registry when installed but when uninstalled fail to remove those changes. Over time, thousands upon thousands of registry modifications slow system performance. A registry cleaner removes those changes. However, in my opinion, registry cleaners cause more problems than they solve. While you might see a tiny amount of performance improvement, for the most part, you’re likely to see glitchy OS behavior after running a cleaner.
The best program out there for cleaning your registry is CCleaner.