Both of these come with a sensor built in that can track your cadence, distance, pace, stride and, of course, steps -- all the important metrics runners care about. Under Armour developed this Record sensor in-house, and it has been drastically improved since it debuted on the SpeedForm Gemini 2 running shoes in 2016; it's now able to track more data than before, such as stride length. The Bluetooth-powered sensors are located inside the thickest part of the midsole, which ensures that they can work even during your rainy-day runs.
As far as power goes, you don't need to worry about charging the HOVRs, since the batteries in the sensors are self-contained. According to Under Armour, the Record chip is designed to outlast the life of the running shoes themselves, so longevity will depend on each individual and how much they work out. That said, the company is confident that you won't ever have to worry about running out of power.
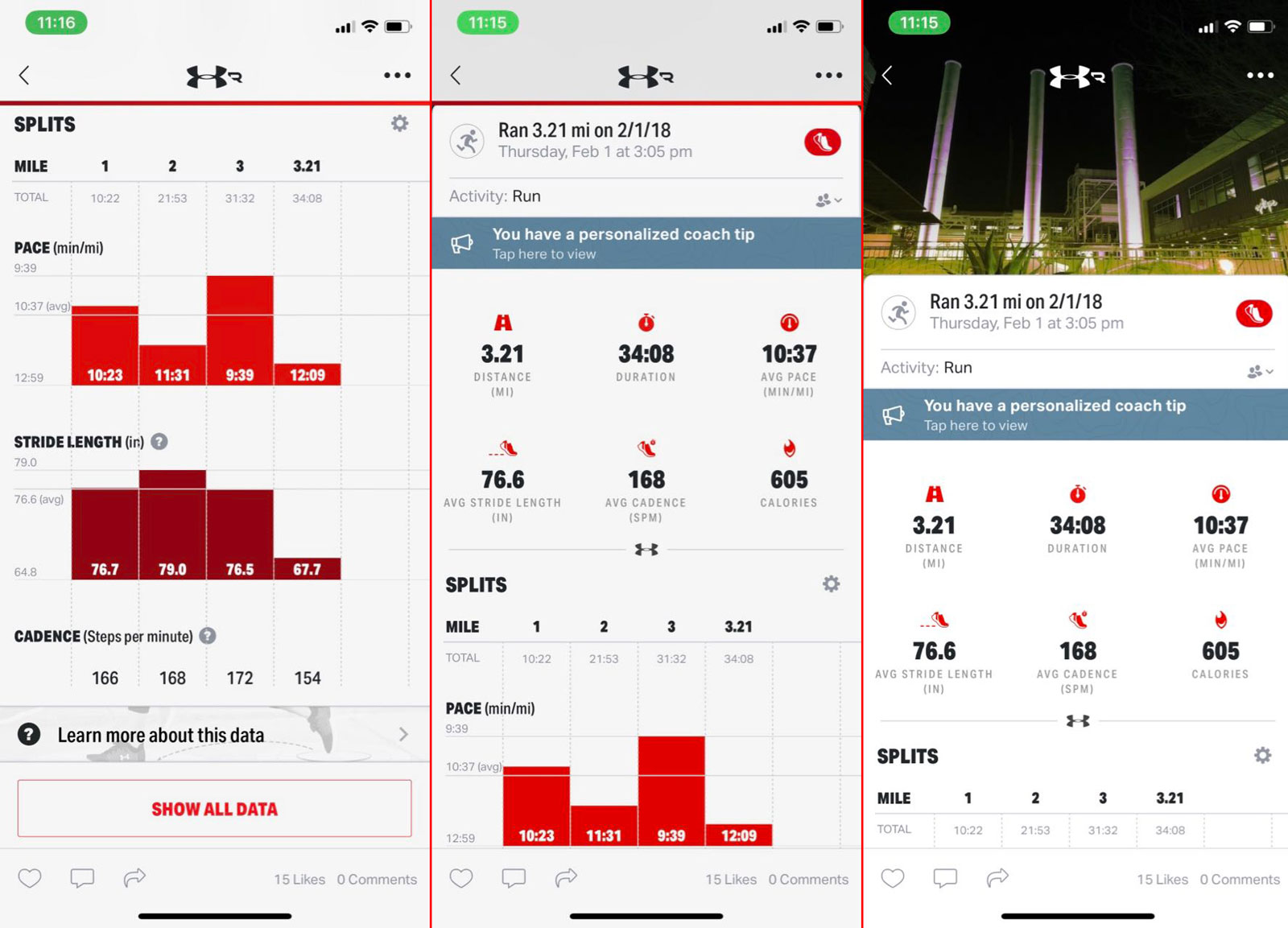
Of course, you'll need an app to digest all the data captured by the shoes. For that, you'll use Under Armour's Map My Run application, available for iOS and Android. Pairing the Phantoms to my iPhone was surprisingly quick and seamless: I took the pair out of the box, placed my phone near them, opened the Map My Run app and, within seconds, a message popped up prompting me to connect my shoes. After I accepted and hit continue, the app pushed an update to them, added them to my "Gear Tracker" tab in Map My Run and then the setup process was complete.
Altogether, it only took about four minutes before my Phantoms were paired to the app. If, for some reason your iOS or Android device doesn't automatically pick up the Bluetooth signal from the HOVRs, Under Armour says it'll give customers a walkthrough of how to connect the shoes to the Map My Run app, which may include telling you to turn on Bluetooth or having to shake the right shoe to wake it up from sleep mode.
One of the main differences between Under Armour's latest Record sensor, compared to the previous version, is that it now lets you go on smarter untethered runs. This means you don't need to have your phone with you with the Map My Run app open to track your stats, since the HOVRs measure your data as soon as you start running. You can then sync that to your app when you get back home if, say, you forgot to take your phone with you. It's a great option for those who like to be as light as possible during their training or workout, or if you simply want to use the HOVRs as an unobtrusive step counter.

Later this month, Under Armour plans to roll out a coaching feature that will add more functionality to the HOVRs and the Map My Run app, both for iOS and Android users. You'll be able to monitor your gait/stride length mile after mile, and the application will show you how that impacts your pace and cadence. Under Armour says that, by interpreting that data, Map My Run can offer you tips on how to improve your pace and splits by changing your form, like if you should be taking shorter or longer strides as you run.
Comfort-wise, the Phantom HOVRs are bouncy yet stiff enough to reduce the amount of impact you feel every time your feet hit the ground. Under Armour says its HOVR foam tech is meant to provide a "zero gravity feel," an element that's complemented by an Energy Web material that's spread through various areas of the shoe's midsole and a knit upper that wraps around your foot like a sock. It's definitely one of the most comfortable running shoes I've tried on, right up there with Adidas' popular Ultra Boost.
The Sonic and Phantom HOVR connected sneakers are available now for $110 and $140, respectively. And if you like the shoes but don't care about making them work with the Map My Run app, Under Armour also has versions without the Record sensor for $10 less per pair.







