You’ve probably already noticed, but Amazon Alexa continues to expand its reach. The personal assistant is just a little more than three years old and has come a long way from its humble beginnings with the original Amazon Echo smart speaker. Oh, how times have changed.
Alexa now powers a whole host of devices and a simple voice command can accomplish some pretty surprising tasks with the right hardware.
We’re highlighting 15 of the best gadgets compatible with Amazon Alexa that you should take a look at in 2018 — from a robot vacuum cleaner to a home coffee maker and everything in between.
1. Garmin Speak

Just say, “Alexa, ask Garmin for directions home.”
Alexa is hitting the road with the Garmin Speak. This compact device, smaller than a deck of cards, attaches to your windshield and connects to your car’s entertainment system using Bluetooth or an AUX cable. Its best feature is definitely the ability to ask Alexa for turn-by-turn navigation guidance. The small screen on the Speak will also show arrows with lane guidance during a trip.
Along with that great perk, the Speak can play music from a number of sources including SiriusXM, Pandora, Amazon Music, and more. You can also control smart home devices, play games, and access the huge and ever-growing catalog of different Alexa skills.
2. Amazon Echo Spot

Just say, “Alexa, wake me up tomorrow morning at 6am to Spotify.”
One of the newest members of Amazon’s Echo line, the diminutive Spot features a 2.5-inch, round touchscreen. A great feature, not found on the larger Echo Show, is a number of different analog and digital clock faces that make the device perfect to use as a voice-controllable alarm clock.
You can take advantage of all the different Alexa-enabled skills using the Spot, such as voice calling and messaging. With a built-in camera, you can also place video calls to other Alexa devices or anyone with the compatible smartphone app.
3. GE Profile P2S930SELSS Cooktop and Oven

Just say, “Alexa, tell Geneva to preheat the oven to 375 degrees.”
It’s time to get cooking with the GE Profile Cooktop and Oven. The P2S930SELSS features an edge-to-edge cooktop surface with extra room for the large pots and pans. There’s even a built-in reversible cast iron grill and griddle. The oven offers accurate heat circulation for evenly baked meals.
And with the Alexa skill, you can control the oven without raising a finger. You can preheat the oven, change the temperature, cancel baking, and more.
Now if Alexa could only clean up the mess afterward.
4. Rachio Smart Sprinkler Controller

Just say, “Alexa, tell Rachio to water the side yard for 2 minutes.”
Smart sprinkler controllers can save homeowners both water and money. Taking the place of a standard irrigation system controller, the smart version can provide better insight on when a lawn needs water and exactly how much.
One of the best choice in the emerging market is the Rachio Smart Sprinkler Controller. Once installed, the Rachio can automatically adjust watering using weather conditions and even more advanced metrics like what’s growing in the location and soil type.
While you can set an automatic schedule, Alexa can also help out. With a voice command, users can start and stop watering, turn on a rain delay, and more.
5. Neato Botvac Connected

Just say, “Alexa, tell Neato to start cleaning.”
The robot apocalypse isn’t here just yet, but you can definitely take advantage of the technology to tackle a mundane home task: cleaning your floors. The Neato Botvac Connected can take care of dirty floors by using special navigation technology that scans the room beforehand to plan the most efficient route while avoiding obstacles.
Using the Alexa skill with the vacuum can make the entire operation handsfree. You can tell Neato when to start and stop cleaning and even instruct the vacuum to return to the charging base.
6. Hunter Signal Ceiling Fan

Just say, “Alexa, turn on my kitchen fan.”
Even ceiling fans are joining forces with Alexa. Along with offering HomeKit support for Apple devices, the Hunter Signal Ceiling Fan also works with Alexa.
Users can control the speed of the fan and dim the lights with their voice. A special WhisperWind motor brings strong air movement without significant noise. Thanks to a reversible motor, you can use the fan all year by changing the direction of the motor in the winter to help keep your home warm.
7. Sonos One

Just say, “Alexa, play Beastie Boys from Spotify.”
If sound quality is your top priority when looking for a smart speaker with Alexa built-in, take a look at the Sonos One. Sonos has always been well-known for top-quality audio, and the SonosOne brings Alexa to the mix.
You can accomplish most everything possible with an Echo device including playing music, controlling smart home devices, and interacting with skills. Buyers can select from a black or white version to better match their home decor. You can use your Sonos One as part of a whole-home audio system with other Sonos speakers, or pair two Sonos One devices together for stereo sound.
8. Sengled Element Classic A19 Starter Kit

Just say, “Alexa, turn the bedroom light to 50 percent brightness.”
Smart lighting is one of the simplest ways to add technology to a home. While the Sengled Element Classic A19 requires a wireless hub, the lights are substantially more affordable than the popular Philips Hue line of products.
The starter kit comes with two dimmable A19 LED soft white bulbs. Using Alexa, you can turn the bulbs on and off along with changing the brightness level.
9. Anova Culinary Sous Vide Precision Cooker

Just say, “Alexa, ask Anova to cook a steak.”
Another kitchen gadget to test your culinary prowess, the Anova Culinary Sous Vide Precision Cooker provides a great way for home cooks to try out the popular cooking method. If you’re unaware, sous vide means food sealed in a bag cooked in a water bath at a consistent temperature. You can cook a surprising amount of items using the method, everything from steaks to soups and even desserts.
With built-in Wi-Fi and Bluetooth, the cooker can be controlled with a smartphone app and also with Alexa. Using Alexa, cooks can heat water to a specific temperature, cook a certain item, or even see how long something has been cooking.
10. EZVIZ Mini O Wi-Fi Camera

Just say, “Alexa, show me the living room.”
A great feature of the Amazon Echo Show and Echo Spot is the ability to view live camera feeds of certain models on screen by just asking Alexa.
Along with night vision, the EZVIZ Mini O Wi-Fi Camera has a 111-degree viewing angle to show exactly what’s going on a room. With a built-in microphone and speaker, you can listen and talk to whoever is near the camera. The camera can also provide alerts on a smartphone when motion is detected.
While a cloud storage option is available to store video, users can also locally store clips using a built-in micro SD card slot.
11. C by GE Sol

Just say, “Alexa, tell Sol to change the light to cool white.”
A very modern take on the usual home lighting fixture, the C by GE Sol is a circular lamp that features on and off scheduling and much more. Users can take advantage of specific light settings that support circadian rhythms and see different visuals for different clocks and timers. You can have the lamp change its shade of white light automatically or manually through a smartphone app.
And while the lamp can be controlled through any Alexa supported device, it’s also Alexa-enabled, so you can play music, interact with skills, and more.
12. Bosch BCM8450UC Automatic Coffee Maker

Just say, “Alexa, tell Home Connect Coffee Machine to prepare a large, extra strong Latte Macchiato.”
Why go to Starbucks when Alexa can act as your personal barista at home? The Bosch BCM8450UC Automatic Coffee Maker needs to be built into your kitchen to operate. If you have the room (and the cash) you’re in for an unbeatable home coffee experience. All you need to add is coffee beans, milk, and water. Then, sit back and enjoy. The machine can create a surprising amount of different coffee styles including ristretto, espresso, cappuccino, and many more.
And while the machine is accessible with a smartphone app, the Alexa voice controls are even easier. Just say what type of coffee you’re in the mood for and the Bosch machine will take care of the rest.
13. Amazon Fire TV

Just say, “Alexa, find a comedy for me to watch.”
Alexa can also act as a remote control when using the new Amazon Fire TV. Along with supporting 4K and HDR content, the streaming video box can tap into a number of different sources including Netflix, Hulu, Amazon Prime Video, and others. Using the included Alexa Voice Remote, you can interact with Alexa and navigate through and find whatever content you’re looking for. You can also use it with Alexa skills as well.
If you have any Amazon Echo device near your television, don’t worry about using the remote.
14. Automatic Pro

Just say, “Alexa, ask Automatic where my car is.”
You don’t need to spend big bucks for a car with smart features. The Automatic Pro is a small device that plugs into a modern car’s OBD-II port for constant power. There’s no need for a smartphone, as built-in 3G service is free for five years.
It can provide real-time vehicle location no matter who is driving a car and also will decode check engine lights and deploy emergency services if a crash is detected.
With Alexa integration, you can ask where the car is parked, if you need gas, and to find out more about your driving habits.
15. Ecobee4 Smart Thermostat

Just say, “Alexa, turn the thermostat to 70 degrees.”
The Ecobee4 Smart Thermostat is currently one of the best choices on the market, and a great way to start building a smart home.
And the device is a double threat. You can control a home’s heating and air conditioning with a simple Alexa command on any compatible device. The thermostat also has Alexa control built-in meaning it can act as a standalone option like the Amazon Echo Dot.
Anyone with Apple HomeKit, Google Assistant, or Samsung SmartThings can also control the temperature of their home using the Ecobee4.

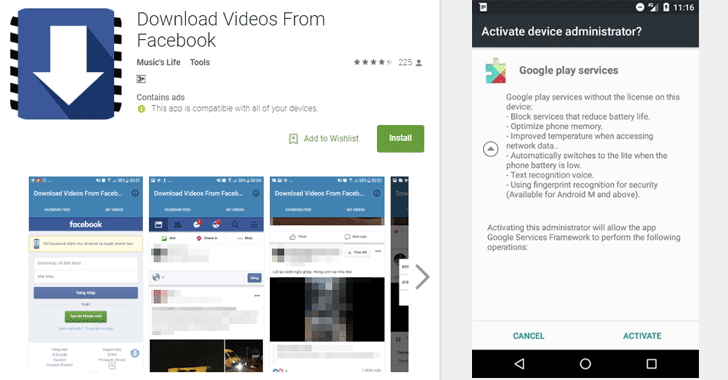





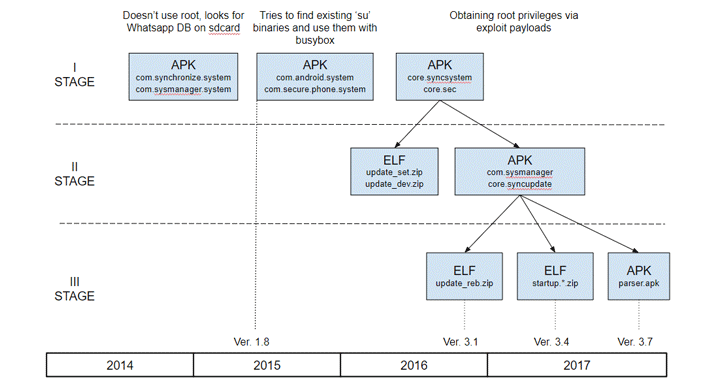
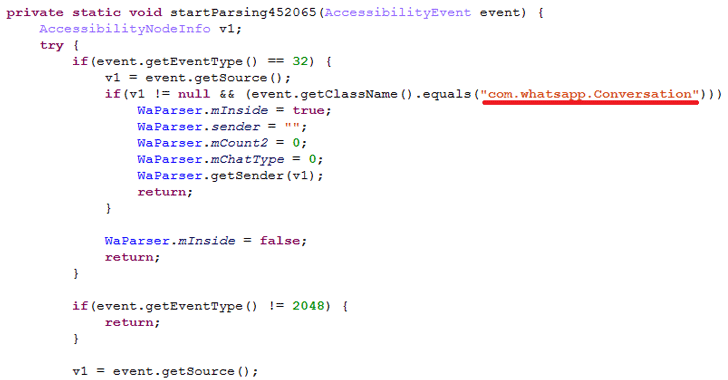

 Direct Messaging
Direct Messaging While such games are good for building imaginations and relationships, they’re also the playground for hackers. Like YouTube, cyberthreats on the websites aren’t the problem. That is, you can’t get a virus just from playing Minecraft, League of Legends or Roblox. You get it when you leave the game’s website and land on another, and thieves use social engineering tricks like the following to lure kids away:
While such games are good for building imaginations and relationships, they’re also the playground for hackers. Like YouTube, cyberthreats on the websites aren’t the problem. That is, you can’t get a virus just from playing Minecraft, League of Legends or Roblox. You get it when you leave the game’s website and land on another, and thieves use social engineering tricks like the following to lure kids away: