There are several threats to children going online for the first time, supervised or otherwise. Before you let them loose, make sure they appreciate the risks by sharing this guide with them. Ensure that they are as capable as you of protecting your family from privacy and personal security risks online. What Is Catfishing? Named after a documentary (see video trailer below) in which the truth and lies of online dating are highlighted, “catfishing” is the insidious act of creating a fake online identity. But this isn’t (usually) a scam to squeeze money out of you. The purpose of catfishing is to fool an individual (typically someone with romantic intentions) and ultimately humiliate them.
https://youtu.be/1xp4M0IjzcQ
So, how is this done? In short, it’s all about digital fakery, with the perpetrator pretending to be someone they’re not. This is achieved by posting false personal information, specifically using some else’s profile pictures, on social media sites. The aim is to trick someone to fall in love with the scammer.
Catfishing is typically aimed at children (mainly teenagers) and young adults, but not always. Regardless of age, you should be concerned about catfishing. Fortunately, there is plenty you can do to reduce (or completely negate) its impact.
1. Make Friends Offline Before you go online, remember the importance of healthy relationships offline. Talking to people face to face, enjoying trips and games — these are far superior to digital exchanges. Although social networking is about communication, verbal, present discussion is far more important and valuable than anything done on a phone or computer.
The digital aspect is really just a gimmick, a shortcut. Keep it genuine. Expanding on this further, it’s not embarrassing or creepy to let your friends meet your parents, or vice versa. It’s useful to put a face to a name. And if a lift to the cinema or a party is ever required, it avoids unnecessary awkward moments.
2. Don’t “Friend” Strangers Getting access to a social network for the first time is exciting. But like anything, you shouldn’t get overexcited. Stick to the same core group of friends that you have at school, or college. If you know a person well in real life, then add them on Facebook (or your social network of choice).
When it comes to strangers, things change. Even if the person is cute/handsome/attractive or whatever, if you have yet to meet them in real life, don’t add. It’s a simple rule that guarantees safety.
Unfortunately, social networks don’t help, throwing up “people you may know”-style suggestions all the time. Incoming friend requests don’t help either. So just remember that rule: Don’t know them? Don’t add them!
3. Set Privacy Controls on Your Social Networks Social networking services come with privacy controls. Typically, these are enabled, but often not to the full extent. As we don’t know which social network(s) you’re using, we can’t possibly go through every single option. However, as a general rule, you should set privacy settings to restrict anyone who isn’t a friend from seeing photos — including the profile pic.
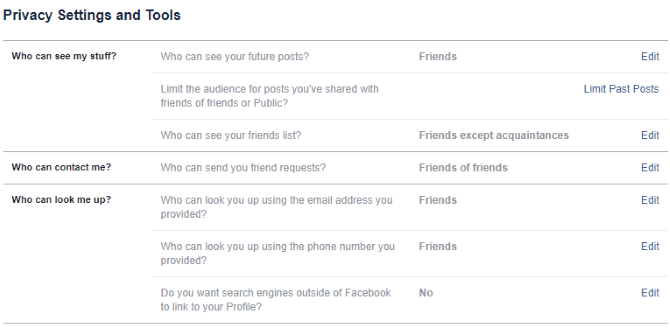 In Facebook, open Settings > Privacy and ensure the options are set to Friends or Only Me. This way, your Facebook account will be protected from being viewed by strangers.
In Facebook, open Settings > Privacy and ensure the options are set to Friends or Only Me. This way, your Facebook account will be protected from being viewed by strangers.
4. Don’t Put Personal Photos on Twitter Access and privacy is a little more complicated on Twitter. Tweets and photos — including profile pics — can be quickly taken out of your control here, thanks to retweets. Within minutes, a photo can go viral, or it can be whisked away for catfishing, before you’ve had a chance to deal with privacy settings.
It’s worth, therefore, opening the Settings page for your Twitter account, going to Privacy and safety, then checking Protect your Tweets. Doing so blocks strangers from viewing your tweets. Anyone who wishes to follow you on Twitter must henceforth be approved. This tightens things up nicely.

Clearing the check against Tweet with a location will help maintain privacy with regards to your location. Meanwhile, you should also select Do not allow anyone to tag you in photos to maintain photo security.
Note that anyone who already follows you prior to protecting your account will still be able to view your tweets and photos. You can, of course, block any of these previous contacts by opening the Followers page, selecting the vertical ellipses, and selecting Block @[username].
You should also disable the option to Receive Direct Messages from anyone, limiting this facility only to your friends.
5. Search Google Images There are at least two victims in catfishing: the target, and the person whose photo is used as a fake profile. Often, these are just models, photos of random attractive people picked up from a Google search. Fortunately, this same tool can be used to track photos.

For instance, if you’re concerned that your profile photo has been misused, you can check. Simply open Google Images at images.google.com, and drag the profile pic from your computer into the browser window. All instances of the photo online will then be displayed.
You can use the same tool to check the photos of your contacts. Of course, you shouldn’t have any followers who aren’t already known to you in real life, but if you do, use Google Image Search to verify their honesty (or otherwise).
6. Delete Inactive Accounts What if you already have a social media account that you’ve forgotten about? Older readers might have a dead MySpace account, leaking their secrets. If you’re younger, perhaps you have an Instagram account that you don’t really use. Either way, these accounts are ripe for farming by catfishing identity thieves.
It can take a while to regain access to old accounts, but it is worth doing so. You’ll often need access to older email accounts, but in some cases, simply being able to recall the setup information (like the name of the email account) will be enough to forward the credentials to your new account.
Once you’ve gained access, delete the photos on the social network profile, and then delete the account
Beyond Catfishing These tips will help shore up privacy holes in a more general way too, giving your child the opportunity to protect him or herself from other online threats.
Moving forward, this whole exercise is a good starting point to safe activity online. Underline the fact that an internet connection doesn’t just deliver the positives of social interaction into your home. The negatives are often included too. Taking steps to mitigate these risks will educate your child, and help to guarantee online safety in future.

